
CanSecWest 2010 banners

Tom Gallagher and David Conger from Microsoft talk about distributed file fuzzing and the Microsoft Office 2010 security model.

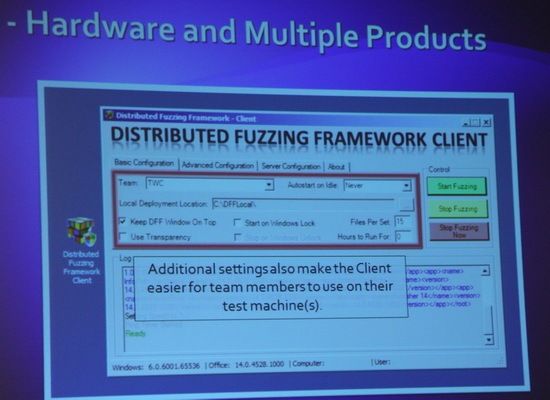

Some other notes from their talk:
- Office supports 300 file formats. each can have different sub formats .wpd extension has 3 different parsers. fuzzing surface=huge
- Microsoft built their own distributed fuzzer system to assist in finding file parser bugs
- Fixed Office bugs by fuzzing (not all sec issues) – 2007 RTM: 1800; 2003 SP3: 600; 2007 SP1: 300; 2007 SP2: 350; 2010 RTM: 1600 via joseph_gan
- File block – push a policy to not allow opening of unused file formats in office
- Gatekeeper dll – file integrity library to protect against unknown vulns in microsoft office 2010
- One more layer of security in microsoft office is protectedview. can run in a sandbox mode.
- winword.exe (1.5mb file size) is a small wrapper for wwlib.dll (25mb file size)

Charlie Miller attacking the Apple Safari browser. Sorry about the colors. Forgot I had a filter on.

Charlie completes a three-peat at the pwn2own contest.


Dragos on the pwn2own phone at the conference floor. “What got owned this time?”
Other pwn2own notes:
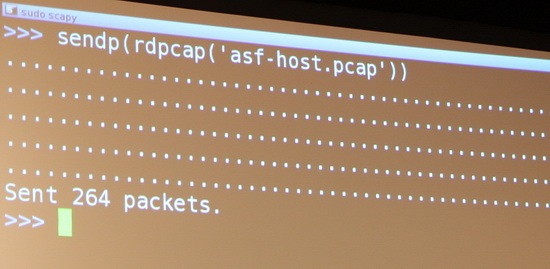
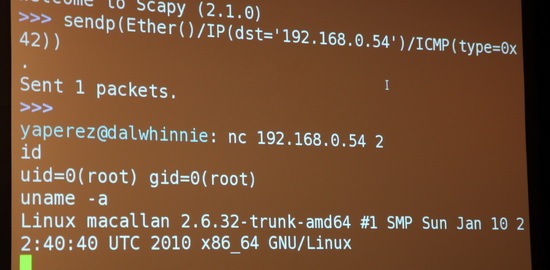
Screenshots from the live demo by Yves-Alexis Perez and Loïc Duflot. The target device was running linux with a Broadcom network card and the exploit resulted in a root shell bound to a port.
Presentation notes:
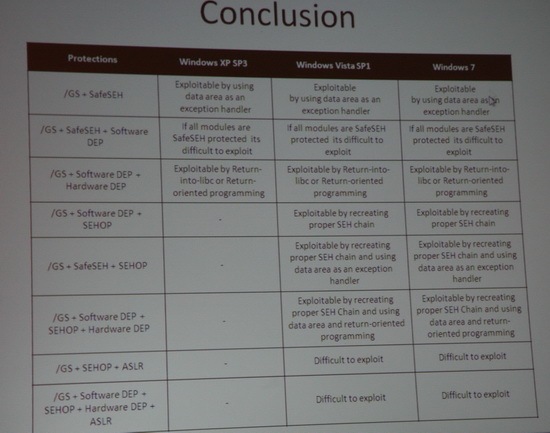
Summary slide from Shuichiro Suzuki’s talk on bypassing Windows protection mechanisms like SEHOP, SafeSEH, /GS, DEP, etc. Some other notes from this talk:
- Bypass SafeSEH and software DEP by utilizing 3rd party librarys that arent compiled with those options
- To bypass SafeSEH you need to recreate the SEH chain in the stack which then references the 3rd party module without safeseh
- The addition of aslr makes it hard to to exploit as you cant recreate the seh chain in the stack
- For aslr/dep exploitation … reference alex sotirov/mark dowds presentation at blackhat usa 2009

Charlie Miller talking about his Python fuzzing setup.
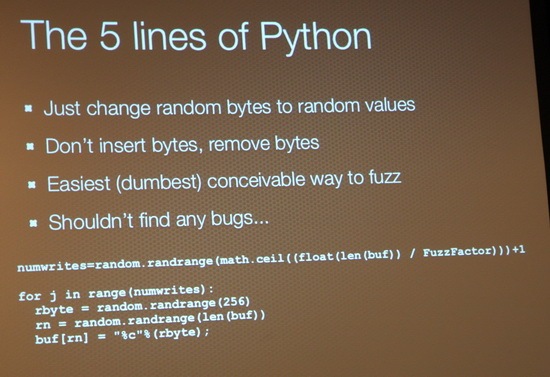
“If you want 0-days, run my 5 lines of Python”, “You’ll find some… I guarantee it!” – Charlie Miller.
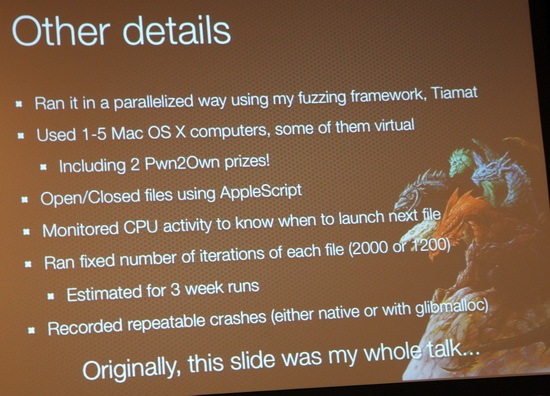
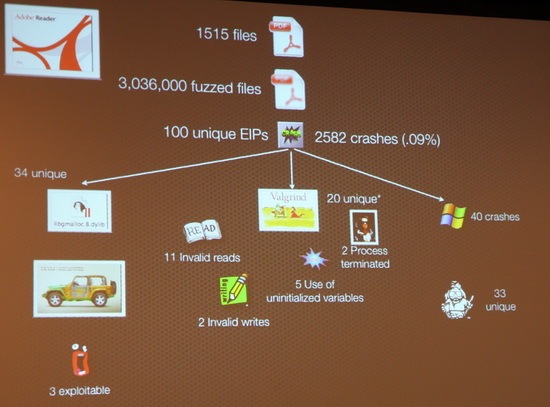
Charlie’s main tools for fuzzing – libgmalloc, crashwrangler, memcheck, !exploitable, valgrind

Adobe reader 9.2, 4 exploitable bugs. Adobe blog post "Fuzzer Lessons Learned" 9.3 had same 4 bugs. Adobe apparently not learning lessons.
Presentation notes:
- "I had to teach my kids not to report bugs to Apple while fuzzing" – Charlie Miller
- “I really wish they would fix this common bug, so i can fuzz easier” – Charlie Miller
- Apple Preview crashed 5.6% of the time compared to .09% of the time with Adobe Reader
- Crashwrangler was accurate 95% of the time on exploitables. !exploitable was only 26% accurate
- Full slide deck at http://securityevaluators.com/files/slides/cmiller_CSW_2010.ppt. It was converted from Keynote, so forgive the formatting.

Halvar Flake and Sebastian Porst the latest project from zynamics.
Presentation notes:
- http://bincrowd.zynamics.com/
- Once you find a vulnerable function in a library, you can ask bincrowd which other programs use this lib as well
- Useful for malware analysis and reverse engineering as it can remember past analysis and import results.save time/effort
- Reqs – idapro 5.6, idapython 1.3.2, bincrowd ida pro plugin at http://github.com/zynamics
- http://lists.darklab.org/pipermail/bincloud/
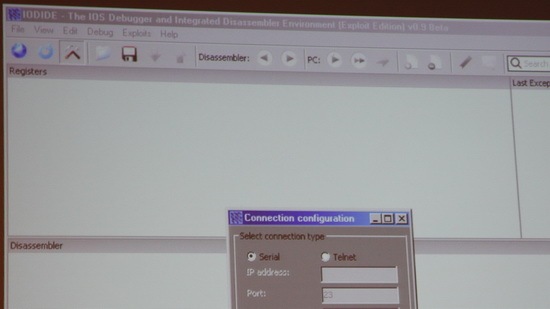
Screenshot of IODIDE – The IOS Debugger and Integrated Disassembler Environment which will be released later this year. Too bad the Exploit Edition which was shown will not be publicly released.

Thorsten Schroeder going over Keykeriki, a wireless sniffer and injector.


The live demo worked which targeted a Microsoft keyboard and injected some commands!
Presentation notes:
- Prefab boards coming at end of year
- http://www.remote-exploit.org/wp-content/uploads/2010/03/keykeriki_v2_cansec_v1.1.pdf

Dr. Melanie Rieback talking about RFID hacking. Presentation notes:
- http://rfidguardian.org/index.php/Main_Page
- Prebuilt RFID Guardian will cost approx. 500 euros
- http://www.openpcd.org/
- http://www.proxmark.org/

Charlie wanted a big check last year so here it is this year. But Charlie leaves for home early! Doh! Well, here is the proof that existed.

Thanks to Dragos and his crew (Yuriko, Will, etc) for putting together another great CanSecWest conference. We’ve been attending for the last four years, and the environment he has created is just top notch. Hope to see you at the next one!
Update: A few more presentation notes:
- Jamie Bulter’s slides – http://fred.mandiant.com/FullProcessReconstitutionfromPhysicalMemory.pdf
- Collin Mulliner’s mobile phone privacy checker – http://www.mulliner.org/pc.cgi

[…] This post was mentioned on Twitter by Garrett Gee and Joseph Gan, Infosec Events. Infosec Events said: #cansecwest 2010 in pictures http://infosecevents.net/2010/03/29/cansecwest-2010-in-pictures/ […]
Social comments and analytics for this post…
This post was mentioned on Twitter by InfosecEvents: #cansecwest 2010 in pictures http://infosecevents.net/2010/03/29/cansecwest-2010-in-pictures/…
[…] image from Charlie Miller’s CanSecWest presentation (credit InfoSec Events) shows how a small home-brewed fuzzing tool found multiple exploitable vulnerabilities in […]